Diagrams of Theory: The Forbidden Triads
View fullsize
>


We are in a podcast bubble – so many podcasts. In a recent episode of This American Life, Malcolm Gladwell discusses whether one shot the basketball underhand or overhand and references an article by Mark Granovetter. The Granovetter article referenced was not The Strengths of Weak Ties (1973) or The Problem of Embeddedness (1985), rather it was his Threshold Models of Collective Behavior (1978). Very few people shoot free-throws underhand, despite it being a superior method. That is, most basketball players have a high-threshold, meaning that they would require a large proportion of other players to begin to shoot underhand before they would start shooting underhand.
But, back to podcasts. Well, first to the forbidden triad.
>


“In the case of three entities, a balanced state exists if all three relations are positive in all respects, or if two are negative and one positive” (Heider 1946:110)
THE PAPER #
Granovetter wrote the The Strength of Weak Ties while in graduate school at Harvard (1965-70). It is one of the most highly cited papers in all of social science, however, surprisingly, it was initially rejected from the top journal in the field, The American Sociological Review, in 1969. Granovetter resubmitted the paper to the American Journal of Sociology in 1972, and it was published the following year (when he was 30 years old). Reading the reviews and Granovetter’s reminiscing in a Citation Classic article (published in 1986, and apparently Granovetter published the original article in Connections in 1982, but I could not find a copy), one can see that the original impetus was to oppose the assumption that modernizing/urbanizing/industrializing societies were increasingly dissolving the social bonds between people. In a word, the paper was about “alienation.”
It’s hard to say what people usually take away from The Strength of Weak Ties, but I’d imagine it is not “alienation” or “social solidarity.” Rather, it is probably, if you share so much time and activities with your close friends and relatives “How much, then, would they know that you don’t already know?” If I wanted suggestions for a new podcast, I won’t ask my friends because they are already listening to the same podcasts as I am!
Harrison White, perhaps the single most influential sociological network theorist and methodologist, was Granovetter’s advisor while at Harvard. He specifically credits lectures given by White on the sociometric studies conducted by Anatol Rapaport and William Horvath. In Rapaport and Horvath’s paper A Study of a Large Sociogram (1961), in which they find that if a researcher asks members of, say, a large school or business, about who their friends or acquaintances are, the first or second choices will result in a much smaller sample of the entire network than if they measured the seventh or eighth. This is because in the first or second choices they tended to select one another. This study by Rapaport and Horvath became the seed for the most widely cited paper in the social sciences.
THE TRIADS #
The triad and transitivity stands at the very heart of this argument. In order to understand the forbidden triad, we have to go back to a time before Granovetter. Interest in the triad is often attributed to Georg Simmel. Part I and Part II of the essay “The Number of Members as Determining the Sociological Form of the Group” was translated into English and published in the American Journal of Sociology in 1902. The main take-away point is, when a third person enters a “dyad” it transforms into a “group,” and the social processes involved are similarly transformed.
>


Johnsen (1985:206)
Building on Heider’s “balance” theory, Cartwright and Harary (1956) formalized the idea that people will tend to seek balance in their relations - so if a triad has all positive relationships, or two negatives and one positive tie, it is a “balanced” triad. Using graph theory, Davis, Holland, and Leinhardt came along and enumerated all logically possible triads by replacing positive/negative relations between people with “directional” relations – or, potentially unreciprocated ties. Rather than balanced or unbalanced, the key distinction is between transitive and intransitive triads.
>


Holland and Leinhardt (1970)
The simple idea of transitivity can be summarized as: the friend of my friend usually becomes my friend. This is because if one person is good friends with two unacquainted others, it is likely these latter two will (a) share similar interests and dispositions, and (b) end up spending time together. Therefore we would say that relationships, like friendships, tend toward “triadic closure.”
>


Davis and Leinhardt (1972:12)
In the classifications of triads, you’ll notice that each possible triad has a label - this is called the MAN labeling system. In this scheme, the triads are labeled according to the number of (M)utual, (A)symmetric and (N) pairs which they contain. For some there is an additional letter which indicates directionality: U for up, D for down, T for transitive and C for cyclic.
>


Davis (1970:844)
From insights about transitivity in social networks, we get a common global measure of network structure: the clustering coefficient. This is basically a fraction of actually observed “closed” triads vs the total number of possible triads (i.e. groups of three people) in the entire network population. Generally, what we find is that human social networks (as opposed to say, computer networks) are highly “clustered” – lots of closed triads. Humans tend to form small “cliques” and have fewer ties outside these groups.
>


Faust (2007:215)
Weak ties #
As many have noted however, social networks exhibit the “small world” phenomena, which means that despite this cliquishness, it usually only takes a couple hops to get from any one person in a network to any other (famously referred to as six degrees of separation). Enter “weak” ties. Up until this point we have been referring to friendship, which is a fairly “strong” tie. What if two people are connected to a shared person only as co-workers? Or any other possible “weak” tie? What Granovetter suggests is that for weak ties the transitive tendency (in other words, the pressure for you to become acquainted with your coworker’s coworker) will be minimized. We should not necessarily expect closure when two ties are weak, but we should when two ties are “strong” ties. Therefore the triad with only two strong ties is the “forbidden triad.”
>
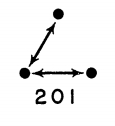

The Forbidden Triad
THE STRENGTH OF WEAK TIES #
One assumption common to network analysis, especially the methodologically innovative work of 1960s through the 1980s, is that what “flows” through a network is some (relatively) undifferentiated and easily transferred substance. This substance is often conceived as information (or knowledge) of some sort (e.g. gossip) or another (e.g. norms). In Granovetter’s own empirical application of the concept to the job market (in Getting a Job: A Study of Contacts and Careers), he finds that people are more likely to find information about job opportunities through weak ties.
With this assumption in mind, it is easy to see that the mechanism for the actual transference is simply the contact between someone who has the information and someone who does not (this is similar to many epidemiological models of the spread of contagious diseases). There is essentially no “transference cost.” If information flows easily from person to person, then those who are more tightly connected (through strong ties within a clique) will very quickly have all the same information. For discovering something new, however, strong ties are weaker or “redundant.” It is here where weak ties are more likely to connect a person to other cliques and less likely to pass on redundant information.
STRUCTURAL HOLES #
>
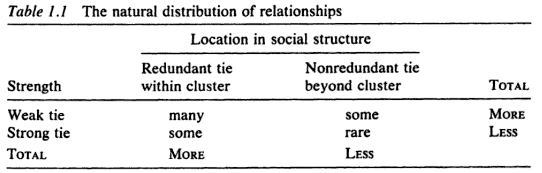

From Burt (1990)
Ronald Burt is well-known for the concept of “structural holes,” which is the absence of ties between two nodes (although he later further specifies a structural hole as the absence of ties between two nonredundant cliques). By focusing on absent ties, Burt both generalizes Granovetter’s key insight that valuable information tends to flow across weak ties. For Burt, a tie becomes valuable if it “bridges” across previously unconnected groups (i.e. the tie spans a structural hole). While this is often (but not always) accomplished by weak tie, as Granovetter argues, not all weak ties span structural holes. In Table 1.1 above, taken from Burt’s Structural Holes, the cell labeled “rare” is Granovetter’s “forbidden triads”. Burt contends that while nonredunant ties are more likely to be weak, he does not forbid the possibility that they are strong, as Granovetter does.
>


The first use of the term “structural hole” that I could find is in a 1986 article Burt co-authored with Miguel Guilarte, titled “A Note on Scaling the General Social Survey Network Item Response Categories.” His more well-known book, Structural Holes: The Social Structure of Competition, was first published in 1992.
RECENT WORK #
In a recent review of one of the most common sources of information about social networks of people in the U.S., the “name generator” on the General Social Survey, Bearman and Parigi (2010) find that the association between network composition and jobs (or other important outcomes) may very well be spurious. Specifically, they find that males report “discussing important matters” with friends and co-workers, while females report family. Therefore, since males tend to have better jobs, one may be attempted to assume the association between weak ties and job information is causal. Based on their findings, Bearman and Parigi conclude that “the association is likely to be an artifact of the asymmetry in the structuring of topics by alters.”
>
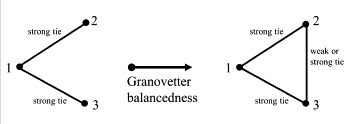

Tutic and Wiese (2015)
Tutić and Wiese (2015) revisit Granovetter’s original article in order to address certain logical shortcomings and consider the difference between the strength of a tie and the value of a tie. In reviewing the concept, they note that empirical applications have often resulted in mixed results, and cannot (without qualification) confirm that weak ties provide more valuable information than do strong ties. Furthermore, they note two drawbacks of Granovetter’s model. First, the strength of ties being ordinal, rather than continuous, means that we cannot posit a relationship between the strengths of of the other two ties and the strength of the closing tie in a triad. In other words, Granovetter presumes that the tie could be either weak or strong. Second, and related, it is unclear how to extend the concept to network structures larger than a triad, such as a quadruple. For instance, in fig. 4 below (taken from Tutic and Wiese), Granovetter’s model could result in an absent, weak, or strong tie while still fulfilling the assumption of the forbidden triad.
>
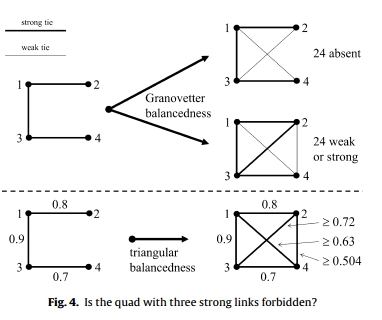

Tutic and Wiese (2015)